I discovered an interesting thing about xor today. It can be used to encrypt data. Depending on how its used, it can be part of the strongest theoretically unbreakable encryption or the weakest.
The first example, where it is the strongest, is when it is used in a “one time pad”. A one time pad is a mechanism for encrypting data. Specifically where the Key data is the same size as the data that you want to send. This is often called the “plain text”. So the three ingredients are the
- “exclusive or”
- Random data.
- The useful data one wants to send.
To represent 2 and 3 I have two images.
The image above is the Key.png this is our random data.
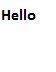
The file above is our data we want to encrypt and send.
 convert Hello.png Key.png -fx “((255-u)&v)|(u&(255-v))” XORHelloKey.png
convert Hello.png Key.png -fx “((255-u)&v)|(u&(255-v))” XORHelloKey.png
The image above is the encrypted version of our data. This was generated by xor’ing the message with our random data. It looks random, I hear you say, and you’d be correct. In fact very correct. You are looking at the “holy grail” of encryption. This is the starting point of where all encryption begins. This is the unbreakable cipher. This is because we have used 100% random data to encrypt it. Ok, so why don’t all systems use this and why does computer code cracking even exist. Well, there is one “huge” downside to this method. You would have to exchange the Key secretly with someone you wanted to send the message to. Needless to say this method is not used today to support https transfers.
Ok whats next? Suppose you could transfer tones of random key data secretly between you and a friend. You could communicate secretly with unbreakable encryption. You could until you run out of secret random data, that is, using this xor method. For if you were to recycle that data just once then all hell breaks lose. The image above is the second message I want to send and the image below is the encrypted xor’d version of it. Using the same key as above.
 convert World.png Key.png -fx “((255-u)&v)|(u&(255-v))” XORWorldKey.png
convert World.png Key.png -fx “((255-u)&v)|(u&(255-v))” XORWorldKey.png
Great looks random enough and it is. However, the fact that the same key has been used twice, means that when they are xor’d together then the image below is produced.
 convert XORHelloKey.png XORWorldKey.png -fx “((255-u)&v)|(u&(255-v))” XORORIG.png
convert XORHelloKey.png XORWorldKey.png -fx “((255-u)&v)|(u&(255-v))” XORORIG.png
And that is the result. It is like looking at a negative. However quite readable. If your on a Linux box you can easily, replay this for yourself using the commands and downloading the image files. Using image magic its possible to “xor” images on the command line. Enjoy.